Top Gun Show welcoming back Ash Kakish
By Access One IncPublished On: May 7, 2025We’re proud to have Ash Kakish, our VP of Channel and Strategic Partnerships, back on the Top Gun Show. As a trusted channel leader, Ash shares why Access One is uniquely positioned in the IT-as-a-Service (ITaaS) space and how we consistently help sales partners grow and succeed. In this episode, he delivers a clear message [...]
Top Gun Show featuring Melondie Vernon
By Access One IncPublished On: May 7, 2025We’re proud to continue our sponsorship of the Top Gun Show with another incredible guest from Access One -Melondie Vernon, MSCS, our Director of vCISO Services. Following recent appearances by Enzo Scafidi and Ash Kakish, this episode dives into the growing demand for Virtual Chief Information Security Officer (vCISO) services. With a Master’s Degree in [...]
Top Gun Show featuring Enzo Scafidi
By Access One IncPublished On: May 7, 2025We’re excited to announce that our very own Enzo Scafidi, Executive Vice President of Access One, was recently featured on the Top Gun Show - which we are proud to sponsor. Enzo is leading the charge in revolutionizing IT-as-a-Service (ITaaS) by empowering Trusted Advisors across the country with Access One’s robust product suite. Our services, [...]
Top Gun Show featuring Ash Kakish
By Access One IncPublished On: May 7, 2025We’re thrilled to share that our very own Ash Kakish, VP of Channel and Strategic Partnerships at Access One, was featured on the Top Gun Show - which we’re proud to sponsor. With decades of experience in channel sales, Ash brings deep expertise and proven leadership to every conversation. In this episode, he discusses the [...]
All Access: A Legacy in Sports and Beyond: Jim Cornelison & Dan Roan Reflect on Their Journeys
By Access One IncPublished On: March 24, 2025Legendary anthem singer Jim Cornelison and veteran sportscaster Dan Roan shared their insights on their careers, the moments that defined them, and their roles as ambassadors for AccessOne.
Why Threat Hunters Are Leaving Traditional SIEM for Real-Time Threat Disruption
By Access One IncPublished On: November 5, 2024Why Threat Hunters Are Leaving Traditional SIEM for Real-Time Threat Disruption Take a journey with me to Anytown, USA where a CEO has just approved the purchase of the latest Security Information and Event Management (SIEM) solution, boasting log monitoring and advanced threat detection. It was a move met with much optimism to strengthen their [...]
The Importance of Having a Recovery Plan in Managed IT Services
By Access One IncPublished On: August 26, 2024The Importance of Having a Recovery Plan in Managed IT Services Let’s start with the obvious questions: What exactly is a recovery plan in the context of managed IT? And why is having one so important? Disaster recovery defined Disaster recovery (DR) is an important part of ongoing business stability, focused on ensuring that the [...]
Recent Incidents Analyzed
By Access One IncPublished On: July 22, 2024Recent Incidents Analyzed Cyberattacks have become infinitely more popular in the years since the pandemic. These attacks don’t just impact smaller companies without the budget or experience to successfully manage their own cybersecurity - they’re happening to major corporations and players in critical infrastructure as well. Equifax paid more than $1 billion in penalties after [...]
Best IT Solutions for a Remote Workforce
By Access One IncPublished On: June 28, 2024Best IT Solutions for a Remote Workforce Making sure that you are able to efficiently navigate the landscape of remote work requires a lot: a mastery of the most cutting-edge tools, a strategic plan, and a genuine desire to encourage both collaboration and productivity in your team. Hybrid (or even fully remote) work isn’t just [...]
How Nonprofits Benefit from Managed IT Services
By Access One IncPublished On: May 24, 2024How Nonprofits Benefit from Managed IT Services Businesses in industries of all kinds have found that they have unique IT needs that go beyond the scope of an in-house department, and nonprofits are no exception. MSPs offer expert IT support that both reduces costs and allows internal teams to focus on the work that needs [...]
5 Factors to Consider When Choosing a Managed Service Provider
By Access One IncPublished On: May 15, 20245 Factors to Consider When Choosing a Managed Service Provider Managing complex, company-wide IT infrastructure while staying on top of new trends, potential threats, and keeping things running day-to-day is a lot to have on your plate, especially if you’re a smaller organization with limited resources. That’s where MSPs come into play. MSPs are companies [...]
Defending the Digital Realm: Navigating the World of Cybersecurity
By Access One IncPublished On: May 3, 2024Defending the Digital Realm: Navigating the World of Cybersecurity We are more online than we ever have been. For the most part, that’s a good thing. Access to most information we need or want is at our fingertips in an instant, and concepts like the Internet of Things make connecting our devices and software to [...]
Why Managed Services?
By Access One IncPublished On: April 16, 2024Why Managed Services? Technology, and what it can do for your business, seems limitless at this point. A slew of advancements like cloud computing and data encryption mean both pros and cons for businesses, though. As technology experiences unprecedented growth, so do potential issues associated with that new technology. Another notable change in the IT [...]
Do You Have a Disaster Recovery Solution in place?
By Access One IncPublished On: March 20, 2024Do You Have a Disaster Recovery Solution in Place? A Disaster Recovery test is invaluable for businesses as it ensures that their disaster recovery (DR) plan is effective and reliable. Businesses heavily rely on data and technology to operate, and any disruption or loss of data can have severe consequences. Therefore, conducting periodic DR tests, [...]
Does Your Internal IT Staff Need Help?
By Access One IncPublished On: March 14, 2024Does Your Internal IT Staff Need Help? Businesses in every industry often find themselves asking this question. In fact, it’s part of a conversation that we have with our potential clients time and time again. It’s important to remember that asking for help is never a bad thing, and it’s no reflection on the capabilities [...]
Cybersecurity Strategy: What You Should and Shouldn’t Do
By Access One IncPublished On: February 20, 2024Cybersecurity Strategy: What You Should and Shouldn't Do It is true that technological advancements of the past decade or so have made it easier to reduce cybersecurity risk to your organization, but hackers and scammers have been advancing on the same timeline. There are no two ways around it, you need to prioritize data security. [...]
Holiday Season Cybersecurity: Lessons Learned in 2023
By Access One IncPublished On: January 12, 2024Holiday Season Cybersecurity: Lessons Learned in 2023 The holiday season means a lot of things - on the one hand, time to relax, recharge and reframe things before the new year. On the other, a lot of hustle and bustle and a mad dash around year-end activities. But to cybercriminals, it means something different. Taking [...]
Preventing Phishing Attacks on Your Business
By Access One IncPublished On: December 28, 2023As technology continues to get smarter and smarter, phishing attacks have continued to get more and more advanced. Business owners of all kinds should be aware of the kind of dupes that spur these attacks, but especially those small enough to have an IT department that is either lacking in terms of manpower or entirely [...]
Why Multifactor Authentication Shouldn’t Make You Roll Your Eyes
By Access One IncPublished On: November 21, 2023Why Multifactor Authentication Shouldn’t Make You Roll Your Eyes Multifactor authentication, the security protocol that asks for more than one form of identification for a login into a secure database or protected account, exists to combat increasingly sophisticated hacking techniques. And while it sometimes seems excessive, it is, unfortunately, necessary. Cyberattacks put private information and [...]
Cloud Migration and Your Business
By Access One IncPublished On: November 7, 2023Cloud Migration and Your Business Let’s start out with the obvious question: What is cloud migration in the first place? We’ve all heard of “the cloud”, a nebulous space that exists somewhere in a global network of data servers that enables users to access the same files, digital assets and applications from almost any device, [...]
October is Cybersecurity Awareness Month
By Access One IncPublished On: October 25, 2023October is Cybersecurity Awareness Month As we navigate through Cybersecurity Awareness Month, it's more crucial than ever to ensure our digital assets are safe and updated. Did you know that Microsoft Windows Server 2012 and 2012R2 reached end of life on October 10th, 2023? Keeping your business current with the operating systems of your servers and [...]
What is Cybersecurity Insurance?
By Access One IncPublished On: October 3, 2023What is Cybersecurity Insurance? Every type of business, from the largest corporations to the family-owned shop down the street, are facing some sort of cyber threat. Preparation is the key to protecting your business - which is exactly why it’s important that no matter the size of your organization, you’re covered with cybersecurity insurance to [...]
IT Support Metrics to Boost Profitability
By Access One IncPublished On: September 27, 2023IT Support Metrics to Boost Profitability Metrics - both qualitative and quantitative - are becoming one of the first indicators of both success and struggle. If we look at the concept of metrics with even more specificity and focus exclusively on IT support, we tend to find some holes. Most corporate leaders don’t really understand [...]
Keep Your IT Security Top-Notch
By Access One IncPublished On: September 13, 2023Keep Your IT Security Top-Notch Keep your IT security top-notch, even when working remotely. Here’s a helpful list of tips from Access One: Use strong passwords that are changed regularly. Avoid passwords like "1234" or "password". Instead, create a complex string of letters, symbols, and numbers that are harder to guess. Don’t reuse passwords from [...]
The Risks of Using Legacy Technologies in 2023
By Access One IncPublished On: September 6, 2023The Risks of Using Legacy Technologies in 2023 Outdated technology is problematic in a sense that goes beyond the annoyance of a poorly-timed crash - and because of the planned obsolescence phenomenon, it’s prevalent for business owners across industries and regardless of budgets. When the competition upgrades, you need to act fast to make sure [...]
Introducing Our Newly Formed Customer Success Team
By Access One IncPublished On: June 26, 2023At Access One, we value customer satisfaction. As our valued client, we are excited to share that we have formed a Customer Success Team dedicated to ensuring you are taken care of throughout your journey with Access One. Our Customer Success Team partners with sales to create a customer centric collaboration. This proactive step highlights [...]
3 Ways Poor Physical Security Can Harm Your Cyber Security
By Access One IncPublished On: January 3, 2023Not all criminals operate in the cyber realm. Implementing strong physical security measures is just as critical to your IT security as firewalls and VPNs. Consider the following statistics:1 88% of business leaders saw an increase in physical threat activity throughout 2022. 83% say unmanaged physical threats have negatively impacted business continuity at their organizations. [...]
How to Enhance Your Cyber Security Posture With Physical Security Solutions
By Access One IncPublished On: December 13, 2022Cyber security measures aren’t enough to protect corporate networks in today’s high-tech world. Physical security is just as vital for protecting digital assets, which is why more organizations are turning to hybrid cloud security solutions that provide real-time alerts, actionable insights, and more to safeguard against cyber attacks. 88% of business leaders reported seeing an [...]
Are Legacy Technologies Holding Back Your Business Growth?
By Access One IncPublished On: October 25, 2022If you've been in business for more than a couple of years, it's likely you're still using legacy technologies. The problem is that technology evolves quickly, and legacy technology can slow the growth of your business. When your competitors upgrade their technology, you could be left with systems that are inefficient, lack adequate security, and [...]
Why You Need to Use Physical Security to Boost Cyber Security
By Access One IncPublished On: August 19, 2022Traditionally, physical security and cyber security were managed by different departments who rarely, if ever, communicated with one another. In today’s environment, the line between the two is blurring, resulting in physical security becoming an essential part of cyber security. What Is Physical Security in the Digital Age? The term physical security is described as [...]
Why Is STIR/SHAKEN Compliance Important for Your Business?
By Access One IncPublished On: July 13, 2022Voice providers are becoming STIR/SHAKEN compliant by using an industry standard for caller ID authentication. The goal is to reduce the number of illegal robocalls – which are a problem whether you’re at home, using your cell phone, or at work. Some robocalls are legitimate. Your pharmacy may initiate a robocall to notify you that [...]
The Top 7 Zero Trust Architecture Benefits
By Access One IncPublished On: June 8, 2022Why should you care about zero trust architecture benefits? Zero trust architecture is a tool you can use to respond to the latest cyber threats. It’s critical because cyber attacks are always on the rise and some traditional tools are no longer effective. For example, the traditional approach of securing the perimeter of your network [...]
The Basics of Network Security
By Access One IncPublished On: April 21, 2022Network security is an important topic for businesses of all sizes and in all industries. Cyber criminals are increasing their attacks at an astonishing rate. For example, there was a 105% global increase in ransomware attacks in 2021, and a 104% increase in North America.1 These attacks weren’t just targeted at enterprise companies. Small and [...]
Microsoft 365 Updates Help Hybrid Workforces Succeed
By Access One IncPublished On: April 7, 2022Since its introduction, Microsoft has been releasing a steady stream of Microsoft 365 updates. In recent years, many of those updates are focused on supporting remote work in response to the significant increase in hybrid and remote workforce strategies companies have adopted since the pandemic. One thing that has changed is the introduction of subscriptions [...]
What You Need to Know to Create a Cyber Security Training Program
By Access One IncPublished On: March 17, 2022Should your business have a cyber security training program? The answer is yes, and it doesn’t matter what industry you are in or if your business is large or small. In fact, 43% of cyber attacks are against small businesses. Companies of all sizes in all industries are increasingly the targets of cyber attacks, and [...]
How to Structure Cyber Security for Your Hybrid Workforce
By Access One IncPublished On: March 17, 2022If your business is one of the many using a hybrid workforce model, you need to focus on cyber security to protect your future. Experts in the cyber security field are concerned about the larger attack surface presented by a hybrid workforce. For example, recent research found that 90% of data breaches1 originated in web [...]
How to Protect Your Company From Cyber Attacks Today
By Access One IncPublished On: March 1, 2022While there are many benefits of doing business online, it can also increase your risks of cyber attacks, security threats, and getting scammed. In an increasingly digital world, businesses should take preventative measures to protect themselves. Cyber attacks can cause serious damage to your business and reputation. Damages can extend to data loss, employee downtime, [...]
What Everyone Needs to Know About Network Security
By Access One IncPublished On: January 19, 2022Every business needs to keep network security top of mind because cyber threats grow more sophisticated and more venomous each day.
Watch Out for These Cyber Security Threats in 2022
By Access One IncPublished On: December 8, 2021Cyber criminals have been busy throughout 2021, and experts are forecasting more attacks targeting vulnerabilities caused by moving to hybrid workforces.
How Real-Time Threat Detection Can Protect Your Business
By Access One IncPublished On: October 20, 2021Cyber threats in 2021 are relentless - there's a hacking attempt made every 39 seconds somewhere on the internet...
How Encryption Prevents Data Breaches
By Access One IncPublished On: October 6, 2021As the world still grapples with and attempts to recover from the COVID-19 pandemic, businesses are exploring several working arrangements for their employees. Organizations that acknowledge in-person work as a necessity and still choose to embrace remote working as an opportunity are gravitating towards a unified approach.
What Technologies Do You Need to Support a Hybrid Workforce?
By Access One IncPublished On: September 13, 2021What technology does it take to make a hybrid workforce successful? Success depends on making it easy for employees to work remotely by providing cloud applications wherever possible and supporting them with: Cloud voice High-speed, always-on access to cloud applications Collaboration tools Robust cyber security Hybrid workforces will succeed when remote workers have the opportunity to [...]
Why the Hybrid Work Model Increases Risks of Cyber Attacks
By Access One IncPublished On: September 13, 2021The hybrid work model is becoming a standard in many businesses, and it describes several work scenarios, including: Some employees work in the office all the time while some work at home all the time Some employees work in the office all the time while other employees split their time between work and home All employees work at [...]
The Hybrid Work Model for Evolving Organizations
By Access One IncPublished On: September 13, 2021The COVID-19 pandemic drove businesses to explore out-of-the-box working arrangements for their employees, including remote and hybrid work. To meet the needs of today’s hybrid workforce, companies like Microsoft have transformed the way they deliver software and technology through updates that support remote work. Hybrid work models, when done right, can make work more flexible, [...]
[Infographic] Proactive Security and Reactive Security
By Access One IncPublished On: April 14, 2021Use these strategies and tactics to ensure that you are effectively managing cyber threats.
Are You Protected Against Cyber Attacks on Small Businesses?
By Access One IncPublished On: April 13, 2021Cyber attacks on small businesses are rampant. Access One explains how to stay protected in this blog.
The Hidden Costs of Cloud Computing
By Access One IncPublished On: March 25, 2021Many businesses don’t have the expertise to avoid the hidden costs of cloud computing. Learn what they are (and how an expert third party can help mitigate them) in this blog.
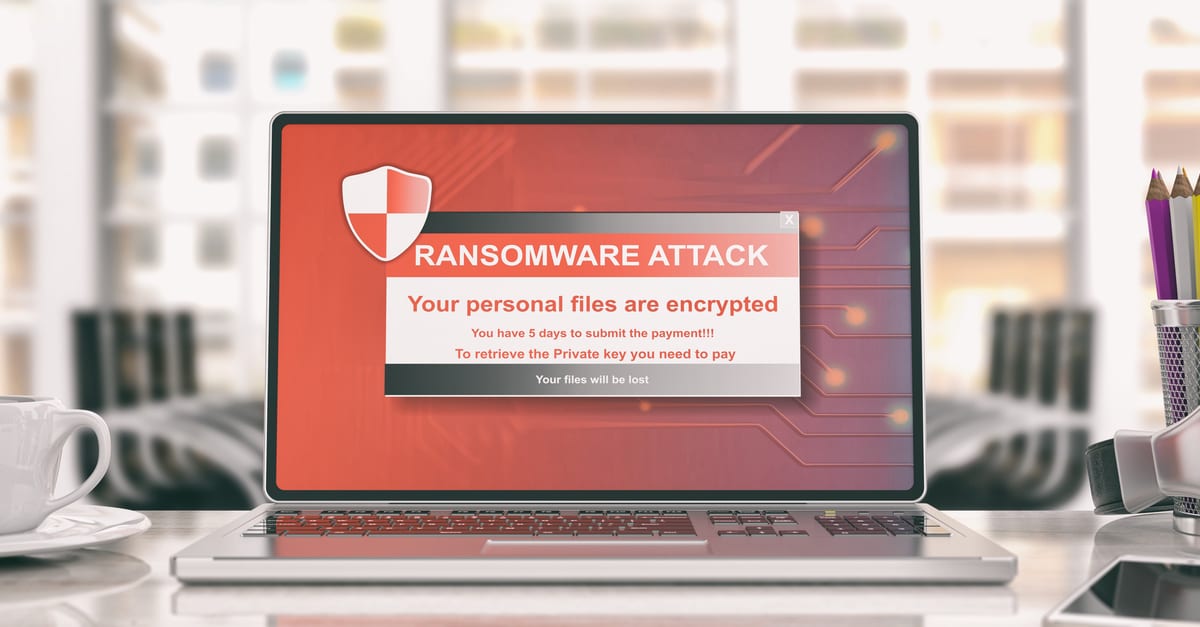
Ransomware Attacks: Why They’re on the Rise and What to Do About It
By Access One IncPublished On: March 17, 2021Ransomware attacks increase in volume and strength as criminals target specific vulnerabilities. Learn more about how to protect your business in this blog.
What You Need to Know About the Cloud and Business Continuity
By Access One IncPublished On: March 2, 2021Cloud and business continuity can ensure your organization suffers no lag in operations should disaster strike. Learn more in this blog.
Do You Need a Cyber Security Risk Assessment?
By Access One IncPublished On: February 18, 2021If you haven’t conducted a cyber security risk assessment this year, you could end up a statistic yourself. Learn how Access One can help in this blog.
What You Need to Know About Colocation vs. Cloud Computing
By Access One IncPublished On: February 2, 2021It’s important to know the differences between colocation and cloud computing before deciding which to implement at your business.
How Effective is Your Employee Training for Cyber Security?
By Access One IncPublished On: January 28, 2021If you’re looking to develop a plan to launch successful employee training for cyber security, read on.
VoIP vs. UCaaS: A Comparison for the Modern Workforce
By Access One IncPublished On: December 11, 2020The terms VoIP (voice over internet protocol) and UCaaS (unified communications as a service) are often used interchangeably. When you’re on the hunt for cloud-based communication technologies, though, it’s important to understand that VoIP and UCaaS are actually two different solutions. This blog explores the key differences.
Managed IT Unpacked: 11 Key Terms to Know
By Access One IncPublished On: December 3, 2020While it is often used in reference to the broad swath of hosted technology solutions available to support business success, there are many sub-categories of managed IT to be aware of. Understanding the managed IT terminology in this post– and the benefits of each service – will help you make more intelligent solutions about your business IT.
Computer Security Tips For Remote Workers
By Access One IncPublished On: November 23, 2020Working outside the office doesn't come with the same safeguards as working on company premises. Here are some best practices to help you and your staff remain safe while remote working.
Why Do You Need a Virtual CIO?
By Access One IncPublished On: November 10, 2020A vCIO is an outsourced technology executive that fills the role of a CIO – without having to pay a full-time CIO’s salary and benefits. vCIOs can focus on the areas where your business struggles the most.
For Seamless Remote Collaboration, You Need Microsoft Teams
By Access One IncPublished On: November 3, 2020One thing businesses have discovered during the COVID-19 pandemic is that, with the right tools in place, employees can be just as productive at home as they were in the office.
Addressing the Needs of the Modern Workforce With Managed IT
By Access One IncPublished On: September 28, 2020Managed IT services give you the tools and support to address the needs of the modern workforce.
Ensure Employee Productivity With Prodoscore
By Access One IncPublished On: September 15, 2020Prodoscore is a cutting-edge tool that provides valuable productivity insights to businesses whether workers are remote or in the office.
What Is Managed Security?
By Access One IncPublished On: August 18, 2020Looking for the answer to the question: what is managed security? Discover the answer – and why smart companies are leveraging it in 2020 – in this blog.
8 Effective Video Conference Tips
By Access One IncPublished On: July 27, 2020Smooth, professional video conferencing requires some effort on your part. Follow these eight tips for a successful experience.
How Managed Services and Technology Help You Work From Anywhere
By Access One IncPublished On: June 9, 2020Businesses navigating any stage of reopening need the support of managed services to succeed.
[Infographic] 5 Best Practices for Remote Work Security
By Access One IncPublished On: June 2, 2020Use these best practices to ensure your employees and data are safe while remote work becomes the norm.
4 Reasons You Need to Backup Data in More Than One Place
By Access One IncPublished On: April 20, 2020To stay up and running in the modern business climate, your business needs to backup data in multiple places.
UCaaS Keeps Your Business Up and Running (No Matter What)
By Access One IncPublished On: April 6, 2020You can keep your business functioning smoothly in any situation with UCaaS.
COVID 19 – Business Updates from Access One
By Access One IncPublished On: March 16, 2020March 18, 2020 An Update on Business Plans – Doing our Part in Chicago, Illinois A letter to our clients, partners, employees, and the overall community: Access One’s top priority is and has always been to serve our community— which includes our clients, our partners, and our employees. By now you’re aware that the only [...]
Are You Ready for Disaster to Strike? Here’s What to Include in Your Business Continuity Plan
By Access One IncPublished On: March 10, 2020Follow these four steps for a business continuity plan that will keep your business up and running in a disaster.
In the New ‘20s, Advanced Business Communication Tools Are a Must
By Access One IncPublished On: March 10, 2020To stay competitive in the ‘20s, your company needs advanced business communication tools.
How to Reduce IT Costs With Managed IT Services
By Access One IncPublished On: March 10, 2020To reduce IT costs, businesses need to make an investment in managed IT services.
Ready for UCaaS? Here Are 4 Reasons to Say Goodbye to Your Legacy Phone System.
By Access One IncPublished On: March 10, 2020There are many reasons to move from your legacy phone system to UCaaS, but these four are the most important.
Access One’s James Fodor Has Joined Liongard’s Advisory Board
By Access One IncPublished On: March 10, 2020James Fodor, Senior Manager of Managed Services at Access One, has joined Liongard’s advisory board.
The Solution to Your IT Team’s Problems: Managed IT Services
By Access One IncPublished On: March 10, 2020Managed IT services can relieve your internal IT staff from daily tasks that take their attention away from more critical operations.
The Top 7 IT Terms You Need to Know in 2020
By Access One IncPublished On: January 6, 2020Know these 7 IT terms to keep up with the pace of change in technology.
MIDMRKT CIO Forum: Get a Year’s Education in Three Days
By Access One IncPublished On: December 4, 2019Access One learns from CIOs at the MIDMRKT CIO Forum: security is a top priority.
Here’s How a vCIO/vCISO Can Help Your SMB Grow
By Access One IncPublished On: December 2, 2019Working with a virtual Chief Information Officer (vCIO) can give small businesses leverage to compete with big ones.
4 Key Elements of Preparing for Cyber Threats in 2020
By Access One IncPublished On: November 15, 2019If you can’t stop all cyber threats, you have to become resilient. Here’s how to prep for – and, with the right precautions, prevent – a cyber attack in 2020.
Switching to Managed Services? Here’s What to Expect From a Managed Service Provider
By Access One IncPublished On: October 18, 2019It’s a fact of modern business: technology is complicated and evolves rapidly. Whether businesses have an internal IT team or not, more and more are discovering the benefit of having the support of dedicated, outsourced professionals with the skills (and time!) to manage the aspects of IT that simply can’t be handled internally.
For an Overwhelmed IT Team, Hiring a Managed IT Provider Is the Answer
By Access One IncPublished On: October 15, 2019Managing information technology is no small feat, even for businesses with a dedicated IT staff. Day-to-day tasks such as patches, updates, and hooking up printers can take up valuable time that could be better allocated toward higher-level projects. On top of that, a fully-staffed IT department with all the knowledge, experience, and specialization required to keep up with shifting technologies can be expensive. According to a survey conducted by Computer Economics, 48% of CIOs believe their IT operational budgets are inadequate.
Key Benefits to Using an Outsourced IT Security Services Provider
By Access One IncPublished On: July 8, 2019Small and mid-size businesses (SMBs) may wonder just how much time and money they need to invest in business continuity and disaster recovery. Especially when headlines so often focus on the breaches affecting large enterprises. In fact, malicious attacks are often conducted against smaller businesses because hackers see them as low-hanging fruit or as a gateway to the bigger enterprises those businesses work alongside. For many SMBs, outsourcing to an IT security services provider can help address these concerns.
Eight Benefits of Outsourcing Your IT Help Desk
By Access One IncPublished On: July 8, 2019If your IT help desk is like that of a lot of enterprises, it probably started out serving a very specific purpose, such as supporting a particular technology. Over time, growing technical needs and additional hires to support them led to a sprawling IT help desk that may no longer be effective at supporting end users.
The Why and How of Implementing Security Frameworks for Your Business
By Access One IncPublished On: June 12, 2019Establishing information security policies in your organization should be your number one priority for a few reasons. As certain industries get more regulated, businesses must be prepared to meet compliance and regulatory demands and demonstrate that they have written policies in place that will keep their businesses protected. Failing to do so – and leaving security behind – can easily translate into bigger problems in the future.
The Pros and Cons of an Outsourced Help Desk May Surprise You
By Access One IncPublished On: May 31, 2019Outsourcing has gathered a few negative connotations over the years, usually because of its close connection to “downsizing” and people who lose their jobs. Outsourcing isn't all about job loss, though; it's also a great way to get something done that you weren't currently doing. An outsourced help desk is an excellent example of this notion, but even as it offers benefits, it also offers potential problems.
Six Benefits of Outsourcing to a Managed Cloud Services Provider
By Access One IncPublished On: April 17, 2019As the impact of cloud computing expands throughout business organizations, many find it sensible to outsource portions of their IT to a managed cloud services provider. Outsourcing involves moving management of cloud solutions and technical support to a provider as a pathway to enhanced business operations.
Six Tips for Choosing a Managed Cloud Services Provider
By Access One IncPublished On: April 17, 2019Once you’ve decided that it makes sense to outsource an area of IT, the next challenge is to choose the right managed cloud services provider. The expertise and offerings of these providers vary widely, with some only supporting a proprietary infrastructure. Others have claimed this expertise to gain a portion of the managed services market [...]
The Ins and Outs of Email Spamming, Phishing, and Security Threats
By Access One IncPublished On: March 7, 2019Long gone are the days of Nigerian princes. Today’s email schemes are clever and are made to deceive even the most adept of us out there.
Addressing Security Fatigue With the Right MSP
By Access One IncPublished On: February 5, 2019Need an MSP that offers security as a service? Learn how Access One is the MSP that can provide a crossover of managed security.
[Infographic] SD-WAN and UCaaS: Better Together
By Access One IncPublished On: January 14, 2019DId you know combining SD-WAN and UCaaS can provide more significant value? Discover how in our infographic.
The Benefits of Investing in a Collaboration Platform
By Access One IncPublished On: December 14, 2018If you’re not investing in a collaboration platform, you’re missing out on the cost savings of video conferencing and the improved productivity of shared workspaces.
A Good Security Strategy Begins With Phishing Prevention
By Access One IncPublished On: December 14, 2018There are plenty of security solutions available, but an effective security strategy begins with training employees in phishing prevention and understanding scams.
Why It Might Be Time to Consider Cloud Communications
By Access One IncPublished On: December 14, 2018When it’s time to upgrade your phone system, there are many reasons to consider cloud communications, from reduced costs to supporting mobility.
Why Mid-Sized Businesses Are Perfectly Positioned to Benefit From Cloud Solutions
By Access One IncPublished On: December 14, 2018Mid-sized businesses are in the perfect position to leverage the benefits of cloud solutions, such as scalability, cost efficiency, and agility.
Comparing Hosted PBX and UCaaS
By Access One IncPublished On: November 15, 2018The choice between hosted PBX and UCaaS often comes down to specific business needs, such as whether you require video conferencing.
Are You Prepared for a Ransomware Attack?
By Access One IncPublished On: November 1, 2018Preparing your enterprise for a ransomware attack includes having an incident response plan and practicing it, and helping employees recognize threats.
UCaaS Benefits: Surprising and Not-so-Surprising
By Access One IncPublished On: November 1, 2018The list of UCaaS benefits is lengthy, and some might not be obvious such as better security and a more professional face for your enterprise.
The Evolution of the Cloud Makes UCaaS Possible
By Access One IncPublished On: November 1, 2018The ability to move communications to the cloud created a host of benefits. UCaaS offers enterprise communications at a lower cost with better features.
[Infographic] 4 Leading Ways UCaaS Helps Improve Your Customer Service
By Access One IncPublished On: October 4, 2018Increase productivity and improve customer service with UCaaS.
Four Items You May Be Missing in Your Multi-Cloud Strategy
By Access One IncPublished On: October 3, 2018Your multi-cloud strategy may seem to cover all the bases, but there are a few common omissions when enterprises make a move to the cloud.
Streamlining Technology Workloads With SD-WAN
By Access One IncPublished On: October 3, 2018With more demand on the network than ever before, SD-WAN offers automation and optimization to streamline network management and troubleshooting.
Why Smart Businesses Are Transitioning to UCaaS
By Access One IncPublished On: October 3, 2018Smart businesses are transitioning to UCaaS as they upgrade communications, gaining both cost savings and productivity while improving collaboration.
Why IT Consulting Should Be in Every Small Business Owner’s Budget
By Access One IncPublished On: October 3, 2018Why you should invest in IT consulting, even if you’re a small business: you’ll avoid headaches like bandwidth shortage down the road.
What Is GDPR? And What Does It Mean For Your Business?
By Access One IncPublished On: September 7, 2018For the past two years, GDPR has been making headlines, most of which detail the challenges faced by companies preparing to meet the demands of this new legislation. Even now, difficulties remain — recent survey data found that 28 percent of organizations still aren’t compliant, and 20 percent are worried they won’t pass their first [...]
Dispelling the Myths Surrounding Cloud Communications Security
By Access One IncPublished On: September 6, 2018Myths abound when it comes to cloud communications security — don’t believe the hype.
Why Enterprises are Migrating to Cloud Communications
By Access One IncPublished On: September 6, 2018Enterprises are migrating to cloud communications, because it offers predictable invoicing, greater reliability, and allows them to access the latest technology.
Five Reasons to Move on from Legacy Phone Systems
By Access One IncPublished On: September 6, 2018A phone system can cost an enterprise in more ways than just the monthly bill. The lack of features could send customers to the competition.
Threat Prediction and Cyber Security: How to Approach Them Proactively
By Access One IncPublished On: September 6, 2018Improving the understanding of threat prediction can lead to better cyber security practices.
Cyber Security Calls for Proactive Security & Reactive Security
By Access One IncPublished On: August 31, 2018When it comes to cyber security, a proactive approach isn’t an option — it’s a necessity.
Ransomware: What It Is, Why It Matters And How To Stop It
By Access One IncPublished On: August 30, 2018What exactly is ransomware? Why does it matter to your organization? What are the risks? And, most importantly, how do you stop it from happening?
Managing Hybrid IT: A Challenge with Great Rewards
By Access One IncPublished On: August 27, 2018Managing hybrid IT is a rewarding task, but one that has plenty of challenges.
Five Items to Consider When Choosing Among SD-WAN Solutions
By Access One IncPublished On: August 8, 2018Choosing between SD-WAN solutions requires a checklist of a few key elements necessary for smooth deployment and daily execution.
The Right Time to Migrate to UCaaS: Considerations for SMBs
By Access One IncPublished On: August 8, 2018Knowing when it’s time to migrate to UCaaS doesn’t have to be a guessing game. Use a clear set of considerations to determine the right approach.
Cyber Security Concerns: The Biggest Threats to Your System
By Access One IncPublished On: August 8, 2018If you have cyber security concerns, know which threats pose the biggest risk to a business.
Six Factors to Consider When Deciding on Hosted PBX
By Access One IncPublished On: August 3, 2018There are several important angles to consider when making the decision to implement hosted PBX.
[Infographic] Managed IT Puts Power into a Digital Transformation
By Access One IncPublished On: July 20, 2018This infographic explains what managed IT can do for a digital transformation.
Five Keys to VoIP Security
By Access One IncPublished On: July 13, 2018VoIP is more affordable and agile than traditional phone services, but comes with risks that must be met with VoIP security measures.
Why Managed Services and Midsized Businesses Are a Good Match
By Access One IncPublished On: July 13, 2018Managed services and midsize businesses make a good match, with companies benefiting from a single point of contact for fulfilling internal talent needs.
Gain a Better Position With Managed IT Services
By Access One IncPublished On: July 6, 2018Managed IT services take the IT burden away from you, providing you with enhanced services, including security.
Gaining IT Resiliency in Your Business
By Access One IncPublished On: May 30, 2018IT resiliency is a tricky thing, but with the right resources at your side, it doesn’t have to be.
Utilizing New Disaster Recovery Techniques
By Access One IncPublished On: May 30, 2018In some cases, taking a new approach to disaster recovery means developing a cloud-based strategy.
Implementing Better Strategies in Light of Cybersecurity Concerns
By Access One IncPublished On: May 30, 2018As cybersecurity concerns continue to mount, being proactive helps keep data safe.
How to Deal with IT Worker Attrition
By Access One IncPublished On: May 30, 2018Turnover rates among IT workers is high. Is it time to outsource?
Cloud Security Relies on Strong Strategies
By Access One IncPublished On: May 11, 2018The cloud is far more than simply a repository for data. It’s also home to applications that many organizations use during day-to-day business operations. That's why cloud security is a top consideration for all organizations. While clients of cloud-based providers are typically attracted to the cloud because it provides them with increased flexibility without requiring [...]
Effectively Managing Enterprise WAN
By Access One IncPublished On: May 11, 2018Cloud solutions, the Internet of Things (IoT), artificial intelligence and increasing data transmissions are all complicating management of enterprise wide area network (WANs). Those findings, based on a recent survey conducted by Versa Networks and Dimensional Research, included 309 respondents discussing how enterprises are managing and securing networks across multiple branch locations. The research also gathered information [...]
The New Role of IT Project Managers
By Access One IncPublished On: May 11, 2018Traditionally, IT project managers would carry assignments through to the point they're ready for handoff to a different department, happy to shake off the dirt off and start fresh with another assignment. Now, however, a new role is emerging in which IT project managers stay involved longer, which comes with certain advantages and disadvantages. The [...]
Cyber Security Tips Everyone Should Know
By Access One IncPublished On: May 11, 2018Remember when cyber security was something only IT workers knew about? That's no longer the case now that bring-your-own-device (BYOD) policies have become more popular and many organizations have embraced digital transformation. These days, it seems like everyone is aware of cyber security issues. And if they aren’t, their systems could be compromised. First and foremost, [...]
How to Improve IT Performance
By Access One IncPublished On: May 11, 2018You’ve communicated your vision for your IT department, provided a clear set of metrics and empowered them to go after specific goals. It’s easy to think that with these key ingredients for building an environment for high IT performance, you should be seeing impressive returns on that investment. Instead, these may be the bare minimum [...]
Why Businesses are Lagging in Terms of Mobile Security
By Access One IncPublished On: May 11, 2018Given the frequency at which cybercriminals are successful at hacking their way into private data, it would seem that every business would make mobile security a priority. However, a recent Verizon survey shows otherwise. Almost 40% of those surveyed said bring your own device (BYOD) is a top concern at their organization, yet only 14% [...]
What Enterprises Need to Consider Before Taking the SD-WAN Plunge
By Access One IncPublished On: May 11, 2018As enterprises contemplate the network changes they require to accommodate a growing number of mobile employees, Bring Your Own Device (BYOD) programs, and cloud technology, many are turning to software-defined wide area networking (SD-WAN). SD-WAN offers solutions to common challenges, such as scalability, the ability to segment different types of network traffic and centralized visibility [...]
Businesses Headed for Digital Transformation Need to Keep Mobile Cloud in Mind
By Access One IncPublished On: May 10, 2018It’s expected that 2018 will introduce more opportunities for businesses to take advantage of the mobile cloud and mobile edge computing. This will introduce new revenue streams and broaden opportunities for offering a variety of features. There is particular excitement surrounding the possibilities involving mobile edge computing, due to the growth of augmented reality, 3D [...]
2017 Technology: A Year in Review
By Access One IncPublished On: December 22, 2017The world of tech is on an ever-faster train of evolution that seems to increase every year. While it’s inevitable this would happen with tech advancements, 2017 was an amazing year when it came to technology. It also held some controversies in this category. […]
Everything You Need to Know About Business Continuity
By Access One IncPublished On: December 19, 2017With the world being more unpredictably volatile lately, have you thought about what would happen if your business faced a disastrous scenario? It’s easy to become complacent on this subject if you’ve never had anything happen to you. However, there’s a first time for everything, and being prepared is essential based on past statistics. [...]
Tips for a Secure Holiday Shopping Season
By Access One IncPublished On: December 13, 2017As stockings are hung and visions of Sugar Plum fairies dance in our heads, it is time to reconsider cyber security as we shop online for gifts for our loved ones.
What You Need to Know About Office 365
By Access One IncPublished On: December 6, 2017Software subscriptions are the new thing - with more and more companies offering the choice between a subscription and outright purchase. It is likely that in the future, subscription will become the only option. Microsoft Office is not alone in offering a subscription option, but should your business use it? For now, at least, it [...]
The Human Firewall – Make Your Employees Cybersecurity Heroes
By Access One IncPublished On: December 1, 2017When we talk about cybersecurity, we tend to think first of anti-virus programs and maybe even adblockers. The weakest link, though, is not software or hardware. The weakest link is always the human element; more than half of security incidents can be linked to an employee who does something negative or who simply makes a [...]
What is the Internet of Things?
By Access One IncPublished On: November 20, 2017Slowly but surely, technology is creeping into every aspect of our lives. We interact with computers before we even leave the house in the morning- think automated thermostats, smart Vs, WiFi connected coffee pots and BlueTooth enabled garage doors. This is the Internet of Things and Machine to Machine communication. M2M stands for "machine to [...]
Securing Your Business – Hardware & Software
By Access One IncPublished On: October 25, 2017Data breaches are big news when they happen to big companies - but devastating when they happen to your company. Cyber security is a concern that every company, of any size, needs to take seriously. If you do not have a cyber security plan, then you need one now. You have two major areas of [...]
Stay Safe with these Cyber Security Basics for Small Businesses
By Access One IncPublished On: October 13, 2017As a small business owner, you probably don't think too much about cyber security. After all, why would anyone attack you when they can get hundreds of thousands of email addresses from Facebook? However, cyber criminals can go after anyone, and if you are handling customer records, finances, bank account information - which almost everyone [...]
National Cyber Security Awareness Month
By Access One IncPublished On: October 10, 2017October is National Cyber Security Awareness Month October has come again, bringing with it colder weather, changing leaves, and thoughts of Halloween candy. For those in the IT world, October is also National Cyber Security Awareness Month, a chance to review the past year, with special focus on security concerns and on ways individuals and [...]
How to Operate Your Business in an Increasingly Mobile World
By Access One IncPublished On: September 29, 2017It’s undeniable that today’s business world is becoming increasingly mobile, thus placing greater demands on growing companies to change their operations. Most transactions and searches that your customers will perform are either online or on their mobile phones. If you’re in the market to capture mobile consumers, then you must keep your firm up-to-date. At [...]
Protect Your Business by Identifying Scams
By Access One IncPublished On: September 21, 2017Your employees are one of the biggest security threats that your business faces–not because they are deliberately sabotaging your business or opening the door to threats, but because they may unintentionally become the victims of a scam. Whether you’re concerned that you might be a victim yourself or you’re ready to train your employees, it’s [...]
What Is SaaS, And What Are Its Key Benefits?
By Access One IncPublished On: September 11, 2017Technology is changing at a more rapid pace than at any time in history—and so is the language we use to describe it. Acronyms abound, from CRM (customer relationship management) to SEO (search engine optimization), PPC (pay-per-click advertising), CTA (call to action) and ERP (enterprise resource planning). And then, there’s SaaS. What is it, and [...]
What to Look for When Hiring an IT Consultant
By Access One IncPublished On: August 30, 2017So you’ve decided that you’re ready to take the leap and hire an IT consulting firm to help take care of your company’s IT needs. Hiring a new IT consultant is a big step for any business, and it’s not one that should be taken lightly. From everyday troubleshooting to ongoing security, you need a [...]
A Quick Guide to Your Organization’s Backup Strategy
By Access One IncPublished On: August 17, 2017When it comes to your organization's vital operational data, backups aren't just a good idea, they're a necessity! Your business relies on a wide range of data in order to accomplish your daily tasks, connect with customers, and more. Without a solid backup structure, a loss of data can lead to costly fixes, excessive time [...]
The Guide to Password Security
By Access One IncPublished On: August 8, 2017Most people do not take the time or effort to make an effective password. In fact, 59% of people reuse passwords over and over or use simple combinations such as “123456”. It’s obvious you don’t want hackers to break into any of your accounts, whether it’s a social media profile or more costly, a bank [...]
4 Reasons Finance Is Embracing The Cloud
By Access One IncPublished On: July 27, 2017The first major public cloud platform became available in 2006, heralding the first wave of cloud adoption. And according to a 2015 survey by Forrester, we are now in the midst of a second wave. This time, after being somewhat tentative in giving up legacy technologies, the finance industry is visibly making its move. Below, [...]
The Right Technology Is the Key to Great Customer Service
By Access One IncPublished On: July 19, 2017Customer service is one of the most important aspects of your business; your customers need to know that when they contact your company, they can expect to receive reliable service every time. As it turns out, customer service is more than just training quality representatives who will be sure to answer questions and respond to [...]
How Managed IT Service Providers Enhance Security
By Access One IncPublished On: July 12, 2017As technology and the Internet continue to grow exponentially, unscrupulous individuals continue to create new security threats for organizational privacy, confidentiality, and data integrity. Because almost all network-based services and applications pose some level of security risk, personal and business information must be protected through enhanced security systems and controls. Managed IT service providers often [...]
Is Your IT Stuck in the Past? Here’s Why You Need to Update
By Access One IncPublished On: June 28, 2017Technology is always changing, but the folks who manage your internal IT may not always go along for the ride. We often hold on to the methods that we’re used to: it’s familiar, comfortable, and generally has a proven track record. The latest and greatest technologies, on the other hand, tend to be full of [...]
Why Your Internet Speed Matters
By Access One IncPublished On: June 14, 2017The Internet has come a long way since its first inception. Due to these advances, the web pages and Internet features have become much heavier than in the past. One web page can have any number of things going on in the background, and a slow Internet connection can wreak havoc on your productivity. [...]
5 Reasons Why Organizations Prefer Managed IT Services
By Access One IncPublished On: June 7, 2017Back in 2015, CNN estimated that up to one million new malware threats were released every day. For example, the WannaCry ransomware attack happened recently. This malware warned users their files would be deleted if they didn’t pay up within a certain timeframe. The WannaCry attack has been one of the biggest malware attacks to [...]
How to Protect Your Small or Medium-Sized Business from Malware
By Access One IncPublished On: May 31, 2017Could your business be hit with a malware attack? The answer, unfortunately, is yes. Whether you’re relatively large or small, and no matter the precautions you take, your company likely has some vulnerabilities that could be exploited with malware. […]
Why You Should be Using Hosted PBX
By Access One IncPublished On: May 17, 2017Private Branch Exchange (PBX) used to be an expensive and ongoing investment that required continual maintenance and training to keep it running smoothly. But now we can harness the power of the Internet to provide a cloud-based Hosted PBX. In this way, the customer is not responsible for all of the stress that traditional PBX [...]
Why Managed IT Services for Healthcare Are a Must-Have
By Access One IncPublished On: May 17, 2017Introduction: The Growing Need for IT Support in Healthcare Managed IT services for healthcare are becoming more important than ever. As hospitals, clinics, and medical offices rely more on technology, they face new challenges—like keeping patient data safe, following strict rules, and making sure systems work smoothly every day. These services help healthcare organizations handle [...]
The Four Major Benefits of Managed IT services
By Access One IncPublished On: April 26, 2017According to CIO and a 2016 study from CompTIA, an increasing number of small and medium size businesses are collaborating with managed service providers to handle some or all of their IT services. There are several reasons for the increased reliance on MSPs, such as cost savings to enhanced security, expedited disaster recovery and the [...]
Cloud Computing 101
By Access One IncPublished On: April 19, 2017The use of cloud technology continues to expand exponentially. With the rise of the Internet of Things, cloud computing has become the next big innovation that tech companies are rushing to adopt. Whether they are transitioning into a cloud-based infrastructure, deploying software, or backing up files, companies are increasingly seeking to benefit from cloud technology. [...]
Cybersecurity Issues Your Small Business Must Prioritize Today
By Access One IncPublished On: March 29, 2017Small businesses used to be able to sit back, secure in the knowledge that they wouldn’t be attacked by hackers, social engineers, or other threats. The fact that they were small kept them from being targets. However, for today’s small businesses, a small size alone isn’t enough protection anymore. Hackers now spend approximately 43% of [...]
Transform Your Phones Into a Sales Driving Machine
By Access One IncPublished On: March 22, 2017What is your first impression when you call a company and get a voicemail message? Especially if the company you’re phoning is a larger firm, not being able to talk to a real person can give you an uneasy feeling and make you think twice about buying. Growing companies often struggle with this issue. Who’s [...]
4 Critical Things to Cover in Your Disaster Recovery Plan
By Access One IncPublished On: March 15, 2017Your disaster recovery plan is the key to keeping your business running smoothly no matter what the crisis is. You need to know how you’ll respond if your business is hit with any type of catastrophe. Technology fails, but your disaster recovery plan can help retain your customers’ and employees’ confidence to ensure that no [...]
5 Reasons to Consider Switching to Hosted Voice
By Access One IncPublished On: February 22, 2017Modern Voice over IP (VoIP) solutions that are hosted entirely in the cloud offer all of the functionality you need, along with productivity-enhancing features, all made possible utilizing a cloud platform. Best of all, it comes with a price savings of up to 80 percent of your current bill. In today’s competitive marketplace, more businesses [...]
7 Common Technology Problems for Small Businesses and Our Solutions
By Access One IncPublished On: February 13, 2017Small businesses face a number of unique technology problems, and Access One understands those problems. We have solutions for common technology issues likely to be faced during normal operations and can keep your technology running more effectively. […]
Top 3 Tips for Mastering Conference Call Small Talk
By Access One IncPublished On: February 8, 2017Conference calls are an essential part to any business person’s day. It’s important to connect with others to talk about business plans, share ideas and information, brainstorm, and more. However, a shocking survey reveals that during conference calls, 65% of people do other work, 63% send emails, 44% text, 25% play video games, and 21% [...]
5 Ways to Eliminate Cyber Criminals
By Access One IncPublished On: January 26, 2017Cybercrime, for many businesses, is one of the greatest threats you’ll have to face. Hackers want to sneak in and steal your data, and if your system is unprotected, you’re offering them an open door that they can walk straight through. Don’t let your business be a victim! If you want to eliminate cyber crime [...]
5 Reasons to Choose Managed IT Services in 2017
By Access One IncPublished On: January 18, 2017Every industry is quickly realizing the key to running a successful business is using new technology to achieve goals. While new technology is helpful and necessary, it is constantly evolving at a rate that many business owners may not be able to keep up with on their own. This is why many businesses are turning [...]
Top VoIP Questions: Answered
By Access One IncPublished On: January 4, 2017Although the term VoIP has become a staple of the business vernacular, there remains some confusion as to what this term references. Also, as a small to medium-sized business owner or decision maker, you most likely have some questions about how VoIP can directly impact and benefit your organization. Let’s dive deeper into the subject [...]
How Managed IT Support Can Grow Your Business Now
By Access One IncPublished On: December 21, 2016Business Now If you had a visual map of your current business landscape, whether a geographical map or a map of economic sectors, which areas would you highlight and target for growing your business? Would you shade a few areas or the whole map? These are important questions, because your amount of shading might give [...]
Benefits of Web Conferencing for the Healthcare Industry
By Access One IncPublished On: December 14, 2016There is no doubt that we have officially entered the digital age. Along with this transition, there are many different technical advancements which benefit virtually everyone - regardless of your industry. One example of this type of advancement is the increased usage of web conferencing. This relatively new technology serves the healthcare industry in three [...]
Law Firms Are Not Immune to Security Breaches – What You Need to Know to Protect Your Clients
By Access One IncPublished On: December 7, 2016When one thinks of data security breaches and the theft of personal information, law firms are not usually at the top of the list of potential victims. Most of us tend to think of banks, hospitals, and credit card companies as “hot” targets. In reality, lawyers very often have access to a wide array of [...]
Thinking About a Colocation Center? Read This!
By Access One IncPublished On: November 23, 2016Considering the digital age that we’re in, there is no debating the importance of data to every business. With that in mind, the physical environment that your organization’s data is stored in can be an instrumental decision regarding natural disasters, security, and cost savings. Many small business owners are not aware that the typical office [...]
A Need For Speed: Rising to Meet Rising Demands
By Access One IncPublished On: November 16, 2016Until Steve Jobs brought his vision of the iPhone to life, people thought there had been nothing new in telecom since 1876 - when Alexander Graham Bell invented the telephone. Scientists are always striving to find new and faster forms of communication, from the telegraph to the radio. And now, people can connect across continents [...]
5 Ways Web Conferencing Can Help Your Business
By Access One IncPublished On: November 16, 2016Web conferencing services can be an invaluable asset for companies both large and small. While email and phone calls are great methods for communication, relying solely on these for exchanging information doesn’t always work. Often, group training and conferences or meetings between multiple parties are required to keep the workload flowing consistently and to ensure [...]
VoIP: 3 Ways VoIP Technology Can Increase Your Productivity at Work
By Access One IncPublished On: November 9, 2016A business owner’s goal should always be to increase productivity – for you and your employees. Some tasks take longer than others, though introducing VoIP technology can help increase productivity in a variety of different ways. Before long, you will wonder what you ever did without it. […]
How Managed Services Outperforms In-House IT
By Access One IncPublished On: November 2, 2016As a business owner, you use technology as part of your everyday routine: printers, computers, routers, and more. As long as those things are running smoothly, you might not even realize how vital they are. Unfortunately, all too often, things stop functioning properly. That’s what your IT team is for. Many business owners assume they [...]
How Managed Services Outperforms In-House IT
By Access One IncPublished On: November 2, 2016As a business owner, you use technology as part of your everyday routine: printers, computers, routers, and more. As long as those things are running smoothly, you might not even realize how vital they are. Unfortunately, all too often, things stop functioning properly. That’s what your IT team is for. Many business owners assume they [...]
Why You Should Consider Outsourcing Your IT
By Access One IncPublished On: October 19, 2016Somewhat recently, if a company needed an IT service they had to perform it themselves, from designing a database to hosting their website. Some businesses still try to do everything themselves. However, the increase in managed IT service providers allows small and medium-sized organizations to outsource many functions. This enables many companies to function well [...]
5 IT Tools Every Small Business Should Be Using
By Access One IncPublished On: October 12, 2016As a small business owner, you have a delicate balance to maintain, customers to satisfy and a corporate vision to maintain. The right IT solutions can help. IT tools exist to manage many of the daily operations of modern businesses. Automated processes tailored to your needs can perform many of the tasks necessary to your [...]
5 Ways Managed IT Services Can Change Your Business
By Access One IncPublished On: October 6, 2016When you're considering how you want to handle your IT services, you have several options. You want a cost-efficient model that allows you to make the most of every day, from quality tech support to the knowledge that your network, servers, and workstations are being managed efficiently even when you're not there to oversee every [...]
Why Unified Communications is Essential for Small- and Medium-sized Businesses
By Access One IncPublished On: July 27, 2016Nobel Prize winner George Bernard Shaw once said, “The single biggest problem in communication is the illusion that it has taken place.” Nowhere is this sentiment more true than in the world of business. We’ve all been there. You’re against a deadline and need to get in touch with an employee who holds the final [...]
Telecom 101: 15 Terms You Need to Know
By Access One IncPublished On: July 20, 2016The telecommunications industry is constantly evolving, and so is the language used to describe it. Unless you work in the industry, remembering all the terms and acronyms can be challenging. And not knowing the basic vocabulary of telecom can make talking to your IT department or service providers difficult. This “need to know” list will [...]
3 Incredibly Useful Data Services for Small- and Medium-Sized Businesses
By Access One IncPublished On: July 13, 2016Today’s small- and medium-sized business (SMB) owners can leverage the Internet to communicate efficiently, increase productivity, and expand their bottom line. But the Internet is vast, and integrating its various services can be tricky for the business leader who doesn’t also happen to be in the know about all things IT. That’s where data services [...]
5 Things SMBs Need To Know When Getting Started with Advanced Storage Solutions
By Access One IncPublished On: July 6, 2016When your business was in its infancy, you might have been able to sustain it with only the storage capacity available on your battered laptop. But, as your business has changed and expanded, so have the tools you use. An exponentially increasing customer base, inventory and order history can quickly bog down standard hard drives, [...]
12 IT Terms You Really Need to Know
By Access One IncPublished On: June 28, 2016It’s common knowledge that technology moves fast. But how fast? The answer is actually daunting. Currently, technology is advancing at an 18-month doubling rate, according to the Massachusetts Institute of Technology (MIT). That means that in a mere year and a half, technology will be twice as powerful as what we have today. And this [...]
Why SaaS Isn’t Your Best Bet for Data Backup
By Access One IncPublished On: June 17, 2016These days, companies turn to SaaS solutions for a range of business needs, from collaboration tools to accounting and payroll to customer relationship management. There are definitely advantages to these SaaS solutions. For instance: […]
4 Things You Probably Didn’t Know About Office 365 But Should
By Access One IncPublished On: June 8, 2016So you’ve ventured into the world of Microsoft Office 365, and you want to make the most of your investment. You’re not alone. Over 22 million people now subscribe to the online productivity suite. With a number of different packages and an ever-expanding menu of applications, it’s easy to feel overwhelmed by this massive product. [...]
The Hitchhiker’s Guide to Managed Services
By Access One IncPublished On: June 1, 2016“Space is big. Really big. You just won’t believe how vastly, hugely, mind-bogglingly big it is.” Douglas Adams, The Hitchhiker’s Guide to the Galaxy You know what else is really big and mind-boggling? Managed services for businesses. With the plethora of service options available, how do you know what your business needs? To help [...]
The Best Phone Solutions for Small Businesses in Chicago
By Access One IncPublished On: May 25, 2016Business phone systems have come a long way over the years. Rather than using traditional landlines, the vast majority of business phone systems now run on Voiceover Internet Protocol (VoIP) networks. Since there are different types of VoIP systems, it can be difficult to decide which, if any, is right for your business. Here’s a [...]
3 Easy Steps Toward Reducing Data Costs and Risks
By Access One IncPublished On: May 18, 2016Most business operations revolve around data, whether it’s developing new marketing campaigns, launching products, budgeting or anything in between. It’s no surprise that companies spend a lot of money to secure their data from risks and the associated costs. On average, small- to mid-sized companies spend nearly 7 percent of their revenue on IT and [...]
The True Cost of IT Downtime
By Access One IncPublished On: May 11, 2016As wonderful as technology is, it’s not perfect. Systems crash, Malware infects software, the Internet goes down and hardware fails. The effects of IT failure are far-reaching. Just one outage can end up costing a business much more than most people realize. According to one survey, IT downtime results in over $26.5 billion in lost [...]
The 6 Technology Issues Almost All Small Businesses Have
By Access One IncPublished On: May 4, 2016Technology in business can be a blessing. Other times, it can feel like a curse. When systems are running smoothly, it leads to growth and better efficiency. However when problems arise, it can bring business to a screeching halt. Having spent years in IT, I can say that I’ve just about seen it all. Here [...]
7 Signs You Need to Fire Your Current Managed IT Services Provider
By Access One IncPublished On: April 27, 2016Face it— owning a business doesn’t make you a technology expert. That’s why so many companies hire managed IT services providers. Not only do they offer timely support at your request, but many also proactively recommend cost-saving services you may not even know you needed. The great thing about outsourcing to managed services providers is [...]
How Remote User Desk Support Can Help Your Staff Be More Effective
By Access One IncPublished On: April 20, 2016Most business owners understand that a business is only as productive as its employees. As such, they continually look for ways to boost productivity and create a more effective work environment. In the IT arena, remote user desk support is one way to help staff be more productive. Remote desktop allows support staff to access [...]
5 Reasons Your Receptionist/Office Manager Shouldn’t be Managing Your IT Network
By Access One IncPublished On: April 13, 2016A growing business always means more —more customers, more revenue and more staff. Most companies rely heavily on technology to keep their expanding business running smoothly. That means managing everything from keeping a website up and running to troubleshooting network problems to ensuring data is kept secure. With so much riding on the successful management [...]
Should You Outsource Your IT?
By Access One IncPublished On: April 11, 2016Great question. In short, it depends. It really boils down to economics. The size of the company is also a critical component in the decision-making process. For large enterprises, maintaining in-house IT resources can come with significant cost advantages, because these organizations typically have the large budgets necessary to grow with technological advancements. The resulting [...]
IT Tips for Office Expansion
By Access One IncPublished On: April 4, 2016As our economy rebounds, businesses are already thinking about expanding to meet future demands. The market is getting more competitive all the time, so being ready for it can mean all the difference for your business. While you may have scouted potential office space or crunched payroll numbers for new employees, it’s easy to get [...]
Network Security Demystified
By Access One IncPublished On: February 19, 2016“The hackers aren’t looking at me - they’re looking at the big guys like Target, Sony and TJMaxx.” I can’t tell you the number of times I have heard this from small to mid-sized businesses. But according to a 2013 Verizon security report, the truth of the matter is that over half of all data [...]
Misconceptions About Disaster Recovery
By Access One IncPublished On: February 2, 2016Far too often, businesses fall into the trap of confusing disaster recovery with data protection. The uninitiated call back memories of their school years, i.e. the failure of their hard drive one week before the thesis deadline. While that is an unfortunate situation, it’s not what disaster recovery is about. The three things most people [...]
Why Remote Monitoring is Essential for your Business Network
By Access One IncPublished On: December 29, 2015One of the biggest misconceptions in network services is about how something called remote monitoring works. Some clients take the term literally and believe that the size of their business doesn’t warrant the need for a simple status checker that has no added benefit. They think: “Well, it’s good that you can see if our [...]
How to (Almost) Future Proof your Telecommunications System
By Access One IncPublished On: December 22, 2015Laura Hanssel – Executive Vice President and Chief Financial Officer, Harris Theater Experience: Over 13 years in the telecommunications field When I first stepped into my job as Chief Financial Officer and Executive VP for the Harris Theater, I looked into upgrading our seemingly ancient landline system. We were approaching a busy holiday season and [...]
A Gloomy Forecast for Reluctant Cloud Technology Adopters
By Access One IncPublished On: December 1, 2015A survey of IT professionals conducted earlier this year found that over 93 percent of respondents use some sort of cloud-based architecture. And with software giants like Microsoft moving towards service-based applications like Office 365, it is inevitable that some users will find themselves left behind because they haven’t made the shift. The subscription model automatically [...]
The Average Cloud Enthusiast vs The Experienced Cloud Operator
By Access One IncPublished On: November 10, 2015At work, Frank uses Gmail, Dropbox, Slack, Trello, and other “cloud-based office applications.” He also uses Microsoft Word, Excel, and maybe a database program from the 90s. Does Frank sound like you? The vast majority of computer users are what I call hybrids. They like having some things in the cloud but are also adverse [...]
The Fast Lane: Telecom 3.0, Turning Business on its Head
By Access One IncPublished On: September 21, 2015Technology has always had a big impact on business. From the printing press revolutionizing the publishing industry to the combustible engine forever changing transportation, technology’s mission is usually to improve efficiency - to make or move things faster. But sometimes, advances in technology go beyond efficiency; sometimes they fundamentally change the way we do business [...]
Telecom Game Changer: Jennifer Fitzmaurice Executive Director – Chief of Staff at AT&T
By Access One IncPublished On: September 2, 2015Have you used your cellphone at a large stadium? What about an underground parking garage that was three levels deep? Ever wondered how you had signal there with no lofty reception towers? You can thank Jennifer Fitzmaurice, current Executive Director – Chief of Staff of AT&T. In her previous role as AT&T’s Director of Construction [...]
Managing Aging Technology
By Access One IncPublished On: July 15, 2015We sat down with Russ Zielezinski, Chief Operations Officer at Advanced Telecommunication of Illinois (ATI) to get his perspective on the challenges of managing aging telecom technologies. Managing aging technology is a challenge that we face everyday with our customers, some of whom operate under the principle, “If it’s not broken, don’t fix it.” But [...]
What You Really Need To Know About Hosted PBX
By Access One IncPublished On: May 15, 2015Technology is advancing every day, and people often have misconceptions about it being expensive and difficult to operate. This simply is not the case when it comes to Hosted PBX telephone systems. The Dark Ages of Plain Old Telephone Service (POTS) for businesses have ended. Although Hosted PBX has been around for years, today’s phone [...]
The Story of Access One
By Access One IncPublished On: May 1, 2015Since opening its doors in 1993, Access One has remained focused on one primary goal: to provide the #1 customer experience in business technology and communications services.
Join our Cybersecurity Webinars this October. Visit our Events Page for details and to sign up.